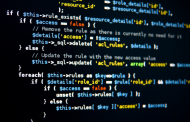
Update : CSRF Fix #3 : https://blog.yakuza112.org/?p=484388 [php] =============================================================== vBulletin 3.X/4.X CSRF IMG-Tag Exploit =============================================================== ___________ .__ .__ _______ \_ _____/ ____ | |__ ____ | | \ _ \ ____ | __)__/ ___\| | \_/ __ \| | / /_\ \ / \ | \ \___| Y \ ___/| |_\ \_/ \ | \ /_______ /\___ >___| /\___ >____/\_____ /___| / \/ \/ \/ \/ \/ \/ # Exploit Title: vBulletin 3.X/4.X CSRF IMG-Tag Exploit # Date: 28/04/2011 # Author: Cyber Tjak # Software Link: http://www.vBulletin.org # Version: 3.X & 4.X # Google Dork 1: Powered by vBulletin 3.X # Google Dork 2: Powered by vBulletin 4.X # Platform / Tested on: Multiple # Category: Webapplications # Code : N/A # BUG : ###################################################################### 1 > Go to something were you want to include it e.g. /profile.php?do=editsignature The IMG-Tag must be allowed there. 2 > Post a new post with these content ===> [IMG]Your Script[/IMG] 3 > You can use it with a plugin like iTrader http://[localhost]/board/itrader_fee...RID&parseurl=1 Furthermore you can use it with external scripts like an ip-logging script. Just like a normal CSRF-Vuln. =) 4 > Now you see that your script is working. # FIX by P4INW4R : ########################################################### You must create a whitelist for trustworthy imagehosters. 1 > Open ./includes/class_bbcode.php 2 > Search for: function handle_bbcode_img_match($link) { $link = $this->strip_smilies(str_replace('\\"', '"', $link)); // remove double spaces -- fixes issues with wordwrap $link = str_replace(array(' ', '"'), '', $link); return '<img src="' . $link . '" border="0" alt="" />'; } # Filled by Yakuza112 : ######################################################### 3 > Replace with: function handle_bbcode_img_match($link) { $link = $this->strip_smilies(str_replace('\\"', '"', $link)); // remove double spaces -- fixes issues with wordwrap $link = str_replace(array(' ', '"'), '', $link); //CSRF FIX // Imagebanana // die Bilder liegen auf den Servern: img1.imagebanana.com bis img7.imagebanana.com // Directupload // s1, s1b,s2, s2b,s3, s3b,s4, s4b,s5, s5b,s6, s6b,s7, s7b,s8, s8b,s9, s9b,s10, s10b,s11, s11b,s12, s12b,s13, s13b,s14 $whitelist = array( "abload.de", "h1.abload.de", "h2.abload.de", "h3.abload.de", "h4.abload.de", "h5.abload.de", "h6.abload.de", "h7.abload.de", "h8.abload.de", "h9.abload.de", "h10.abload.de", "h11.abload.de", "imagebanana.com", "img1.imagebanana.com", "img2.imagebanana.com", "img3.imagebanana.com", "img4.imagebanana.com", "img5.imagebanana.com", "img6.imagebanana.com", "img7.imagebanana.com", "img8.imagebanana.com", "img9.imagebanana.com", "img10.imagebanana.com", "directupload.net", "s1.directupload.net", "s2.directupload.net", "s3.directupload.net", "s4.directupload.net", "s5.directupload.net", "s6.directupload.net", "s7.directupload.net", "s8.directupload.net", "s9.directupload.net", "s10.directupload.net", "s11.directupload.net", "s12.directupload.net", "s13.directupload.net", "s14.directupload.net", "s1b.directupload.net", "s2b.directupload.net", "s3b.directupload.net", "s4b.directupload.net", "s5b.directupload.net", "s6b.directupload.net", "s7b.directupload.net", "s8b.directupload.net", "s9b.directupload.net", "s10b.directupload.net", "s11b.directupload.net", "s12b.directupload.net", "s13b.directupload.net", "s14.directupload.net"); $host = parse_url($link, PHP_URL_HOST); if(substr($host, 0, 4) == "www.") { $host = str_replace("www.", "", $host); } if (in_array($host, $whitelist)) { return '<img src="' . $link . '" border="0" alt="" />'; } else { return '<p style="color: red;">Please upload your picture at a trusted hoster. For example abload.de</p>'; } } We know that this fix-method is suboptimal so we must wait for a better fix by vBulletin. ################################################################################ Our Website: http://www.echel0n.net https://blog.yakuza112.org Special Thanks to: P4INW4R, Subnet, Skittles, 0x00, Santa & all other mates. ################################################################################ [/php]
CSRF Fix #2
Über den Autor
Ähnliche Artikel
© ¥akuza112 Inc. 2010 - All rights reserved.


2 Kommentare
¥akuza112
updated : http://paste.yakuza112.org/?5722ee8a960a9d73#3S57OLMH02zSzaFHr3KD67+cgeSZTDM48dvru5mhXi8=
¥akuza112
Ein herzliches Danke geht raus an Unnex :
Script wurde nun so abgeändert, das man nicht alle einzelnen Subdomains manuell eingeben muss : http://uniquecrew.net/showpost.php?p=61915&postcount=6