Translated In english
Good Tip And Tricks For Binary Crew
Credits / Originated From Indetectables.net
What is Malware?
Within the malware term encompasses all kinds of programs designed to steal information, remote control system or other malicious actions carried out without user consent. Within the malware term encompasses all kinds of programs designed to steal information, remote control system or other malicious actions Carried out without user consent. It is called malignant or malware program for their usual destructive properties. It is called malignant or malware program for their usual destructive properties.
Types of Malware Types of Malware
There are many types of malware, essentially one can distinguish the following: There are many types of malware, essentially one can Distinguish the following:
Virus: A virus is a parasite program adds itself to another program in order to infect or add an unwanted function. Virus: A virus is a parasite program adds itself to another program in order to infect or add an unwanted function. Viruses can be very destructive capacity according to their classification. Viruses can be very destructive capacity according to their classification. Some are easy to detect and therefore difficult to detect and remove. Some are easy to detect and Therefore difficult to detect and remove. Some viruses use polymorphism (change shape) to mutate into new forms and prolong their stay while they are detected. Some viruses use polymorphism (change shape) to mutate into new forms and prolong their stay while they are detected. A virus requires the assistance of the user in order to be executed, so that use of deception to trick the user to run a program harmless. A virus requires the assistance of the user in order to be executed, so that use of deception to trick the user to run a program harmless.
Trojans: A Trojan is malware that performs actions to control the compromised user’s system, giving the attacker complete control over the machine. Trojans: A Trojan is malware that performs actions to control the compromised user’s system, giving the attacker complete control over the machine. As its name suggests, the Trojans typically up to the system embedded within other software. As its name suggests, the Trojans typically up to the system embedded within other software.
Worms: A worm is a virus with the ability to propagate itself, these do not require part of the user interaction to spread throughout the system. Worms: A worm is a virus with the ability to propagate itself, these do not require part of the user interaction to spread throughout the system. In recent years there have been very common, but still used for other purposes such as distributing trojans and other malware into devices such as USB, CD or software in the network. In recent years there have been very common, but still used for other purposes such as distributing trojans and other malware into devices such as USB, CD or software in the network.
Spyware / Adware: Spyware and adware are described as a kind of software that is installed without user consent in order to report the behavior of the user to the attacker. Spyware / Adware: Spyware and adware are described as a kind of software that is installed without user consent in order to report the behavior of the user to the attacker. The attacker in this case uses the malware to advertise products, report bugs or display false security alerts to the user, for this download some kind of malicious content to your machine. The attacker in this case use the malware to advertise products, report bugs or display false security alerts to the user, for this download some kind of malicious content to your machine. Although it is obvious that these alerts, the user falls and makes way for more malware such as keyloggers, screen personal data, etc.. Although it is obvious that these alerts, the user falls and makes way for more malware such as keyloggers, screen personal data, etc. .. As they are considered highly dangerous. As they are considered highly dangerous.
Rootkit: The definition of „rootkit“ has evolved, today refers to a category of software that hides itself. A rootkit is a tool, or a toolkit which aims to hide herself in the operating system and hide other programs, processes, files, directories, registry keys, and / or ports. Rootkit: The definition of „rootkit“ has evolved, today refers to a category of software that hides itself. A rootkit is a tool, or a toolkit Which aims to hide itself in the system operating and hiding other programs, processes, files, directories, registry keys, and / or ports. These are often used to ensure an intruder still have access to a system once it has successfully entered the first time. These are often used to Ensure an intruder still have access to a system Once it has successfully entered the first time.
Initial analysis of malware
Recommended for Windows Analyzers Analyze recommendations for Windows
Since malware can have many behaviors, it is recommended to use an application that integrates and record all these actions. Since malware can have many behaviors, it is recommended to use an application that integrates and record all these actions. Among many that are available as the tools from sysinternals and iDefense, the recommended is this: Among many that are available as the tools from sysinternals and iDefense, the recommended is this:
SysAnalizer: Integra sniffer connections, monitoring APIs, processes and registry changes. SysAnalizer: Integra sniffer connections, monitoring APIs, processes and registry changes. The full tool to have all the information The full tool to have all the information
http://docs.google.c…62g_8gcctsccj_b
When you start the analysis with this tool, guide us step by step through the information generated in a visual manner with the option of seeing first-hand details of the actions of the malware on your computer. Information as active processes, active ports, processed DLLs, drivers loaded, recording changes in regedit, files and APIs are available so we have to know the behavior of malware. Information as active processes, active ports, processed DLLs, drivers loaded, recording changes in regedit, files and APIs are available so we have to know the behavior of malware.
http://docs.google.c…62g_9hmcc384p_b
SELECTIVE ANALYSIS OF SELECTIVE BEHAVIOR OF MALWARE MALWARE ANALYSIS OF BEHAVIOR OF
You can make individual tests as we want to know about malware, You can make individual tests as we want to know about malware,
for this there are many other useful tools which we will see below: for this there are many other useful tools Which Will see below:
Analyzing malware protection type: Analyzing malware protection type:
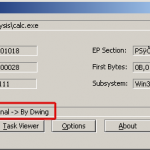
The first thing you should know is to determine what type of file is malware. The first thing you should know is to determine what type of file is malware. Tools such as SIDS, or RGD Packer QuickUnpack detector are very useful to know whether the file has some kind of encryption, protection or modification. Tools like PEiD, or RGD Packer QuickUnpack detector are very useful to not know whether the file has some kind of encryption, protection or modification. This tool has signatures to detect the type of packaging and provide a simple interface to unpack. This tool has signatures to detect the type of packaging and Provide a simple interface to unpack. In case you can not do with these tools you can use a more complex manual unpacked using a debugger to see how the tool behaves and unpack (OllyDbg, IDA Pro, etc). In case you can not do with these tools you can use a more complex unpacked manually using a debugger to see how the tool behaves and unpack (OllyDbg, IDA Pro, etc).

Analyzing active processes:
The malware to be executed can launch several processes, it helps to know who is running to identify new processes that are generated and so know which one is done evil actions, as sometimes used by malware phishing system processes to go unnoticed. The malware to be executed can launch several processes, it helps to know who is running to identify new processes that are generated and so know which one is done evil actions, as sometimes used by malware phishing system processes to go unnoticed. Tools like Process Explorer from Sysinternals, Process Analyzer allows visually see the active processes in the system and identify which of these firms is evil so we can finalize it or analyze it thoroughly. Tools like Process Explorer from Sysinternals, Process Analyzer Full Version visually see the active processes in the system and identify Which of these firms is evil so we can finalize it or analyze it thoroughly.
These tools memory dump in search of new changes and quickly identify malware processes created to execute based on a preconfigured signature database, this in order to differentiate from other system processes that act as impostors of the same. These tools memory dump in search of new changes and quickly identify malware processes created to execute based on a preconfigured signature database, this in order to differentiate from other system processes that act as impostors of the same.
http://docs.google.c…62g_5g87bbjd7_b
Analyzing system API calls:
A malware can be named as the calls you make to the APIs of the system, so you can set that uses or makes behavior using resources from other programs or the same system. A malware can be named as the calls you make to the APIs of the system, so you can use that in September or behavior makes using resources from other programs or the same system. Calls to APIs as opposed to processes can easily go unnoticed because they are calling. Dlls or injected under the same procedures. Calls to APIs as Opposed to processes can easily go unnoticed Because they are calling. Dlls or injected under the same procedures. Tools and API Logger (included in SysAnalizer) can obtain complete information on this type of behavior and identifying malware easily. Tools and API Logger (included in SysAnalizer) can Obtain complete information on this type of behavior and Identifying malware easily.
Where to find API calls we can clearly identify suspicious objects or processes that are invoked in the same (very common in injection methods) Where to find API calls we can clearly identify suspicious objects or processes that are invoked in the same (very common in injection methods)
http://docs.google.c…62g_6gsbfsqfh_b
Analyzing changes in files:
You can get clear of the changes that generates a malware to be executed by keeping track of files that are modified after it is executed. You can get clear of the changes that generates a malware to be executed by keeping track of files that are modified after it is executed. Tools such as FileMon are an easy way to find changes in the system. Tools such as FileMon are an easy way to find changes in the system. Additionally, searches can be known malware makes folders and directories. Additionally, searches can be known malware makes folders and directories. Sometimes malware is programmed to make changes not immediately but after a while, so it is essential to maintain a complete record of activities from the time of execution of malware so far shutdown to know the changes. Sometimes malware is programmed to make changes not immediately but after a while, so it is essential to maintain a complete record of activities from the time of execution of malware so far shutdown to know the changes.
Analyzing the program strings
A string is a string of text, analyze text strings that are visible in a program can give us an idea of its operation. A string is a string of text, analyze text strings that are visible in a program can give us an idea of its operation. For this we use a hex editor as HxD or program that extracts the strings from the application, as the strings from sysinternals and have quickly learn about the program content. For this we use a hex editor or a program as HxD that extracts the strings from the application, as the strings from sysinternals and have quickly learn about the program content. If the program is protected / encrypted we can not have a clear picture of the strings, so you need to unpack or unprotect them legible. If the program is protected / encrypted we can not have a clear picture of the strings, so you need to unpack or unprotect them legible.
http://docs.google.c…2g_10t93c4ccj_b
Analyzing movements in the log:
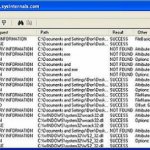
Regshot is an open source application, very light and that it meets its goal quite well in just a few minutes, also requires no installation. Regshot is an open source application, very light and that it meets its goal quite well in just a few minutes, also requires no installation. Not only is limited to verify changes within the Windows registry, is also able to verify the changes made within any system folder. Not only is limited to verify changes within the Windows registry, is also able to verify the changes made within any system folder. Thus we see that values are added to the registry, which keys were modified, added files with your path and file attributes have been modified. Thus we see that values are added to the registry, Which keys were modified, added files with your path and file attributes have been modified.
http://yuntaa.com/Ph…040A8C003026B3C
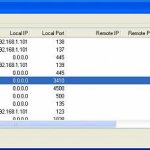
Analyzing active connections:
It is very useful to know which links are displayed when you run a malware, such as in the case of Trojan connects to any IP address or port have been executed once, so having a complete record of our connections and that these processes generate TCP or UDP can quickly identify a potential threat or attempt to connect. It is very useful to know which links are displayed when you run a malware, such as in the case of Trojan connects to any IP address or port have been executed once, so having a complete record of our connections and that these processes generate TCP or UDP can quickly identify a potential threat or attempt to connect. Tools such as Active Ports or a simple netstat can help us in that order. Tools such as Active Ports or a simple netstat can help us in that order. Another program that we use is TCPView from sysinternals. Another program that we use is TCPView from sysinternals.
Analyzing traffic generated by connections:
Sometimes not enough to know which port connects to a malware to identify their behavior, so that you can use sniffer traffic generated in these connections and learn what information is being sent as packets that are caught in communication. Sometimes not enough to know which port connects to a malware to identify their behavior, so that you can use sniffer traffic generated in these connections and learn what information is being sent as packets that are caught in communication. Many sniffers like wireshark allowed to inquire, but that process to identify the connection goes further facilitates the task, it lets us know what type of malware is connecting to IPs and others. Many sniffers like wireshark allowed to inquire, but that process to identify the connection goes further Facilitates the task, it lets us know what type of malware is connecting to IPs and others. Applications like SnifHit give us complete information about them. Applications like SnifHit give us complete information about them.
For IRCbots for example, we know that connecting channel, which sends commands and all this information will be detailed. For IRCbots for example, we know that connecting channel, Which sends commands and all this information will be detailed. Or if UDP connections are difficult to sniffer will be similar. Or if UDP connections are difficult to sniffer will be similar.
http://docs.google.c…62g_7cc6cs6d2_b
Rootkit
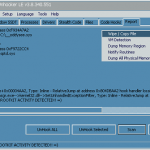
Because rootkits work differently common malware, specialized tools are needed to detect hooks, modifications to the service table (SSDT) and detection of hidden codes. Rootkit Unhooker LE (RKU) is an advanced utility for rootkit detection and removal, this allows for an advanced vision of service tables, stealth code, hooks on drivers, libraries, IAT / EAT, DKOH, IRP, and kernel executions other methods that use rootkits to stay in a system. Because rootkits work differently common malware, specialized tools are needed to detect hooks, modifications to the service table (SSDT) and detection of hidden codes. Rootkit Unhooker LE (RKU) is an advanced utility for the detection and removing rootkits, Allows for an advanced this vision of service tables, stealth code, hooks on drivers, libraries, IAT / EAT, DKOH, IRP, kernel executions and other methods that use rootkits to stay in a system. By the way „report“ makes a full summary of the analysis of all these elements, filtering hooks and potential suspects or rootkits. By The Way „report“ makes a full summary of the analysis of all these elements, filtering hooks and potential suspects or rootkits.

Online malware analysis
There are several websites that allow users to know with certainty the behavior of a file to be executed without compromising the security of your machine. There are several websites that allow users to know with certainty the behavior of a file to be executed without compromising the security of your machine. These generate a complete log which gives an idea of the behavior of malware to be executed. These generate a complete log Which gives an idea of the behavior of malware to be executed. Although not entirely accurate because some malware detection Defense implement virtualized environments, so do not execute when all its functions are analyzed by such tools. Although not entirely accurate Because some malware detection Defense implement virtualized environments, so do not execute when all its functions are analyzed by such tools.
> swap
Analysis using CWSandbox

Analysis using Anubis

Analysis using Sunbelt
Analysis using ThreatExpert

Source : http://www.hackhound.org/forum/tutorials/article/165-binary-crew-tips-malware-analysis/










2 Kommentare
mlevi2538
new site:
http://malwareanalysis.org/
Yakuza112
thanks :D